Cisco Umbrella Policies That Stop 90% of Phishing Clicks (Real Configs Inside)
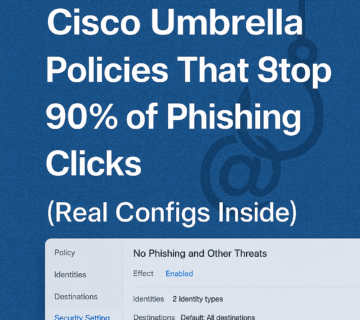
Cisco Umbrella policies to combat the pervasive threat of phishing, particularly for small and medium businesses (SMBs). It outlines seven specific real-world policy configurations ranging from aggressive to balanced, designed to block up to 90% of phishing attempts by leveraging DNS-layer security. Furthermore, the text details advanced techniques such as SSL decryption and Intelligent Proxy and offers a structured, multi-phase deployment methodology, including common pitfalls to avoid. Finally, the source concludes with an advertisement for Technijian, a Managed IT Services provider that offers professional deployment, ongoing management, and strategic security planning to assist SMBs with their Umbrella implementation and broader cybersecurity needs.
... Read More



