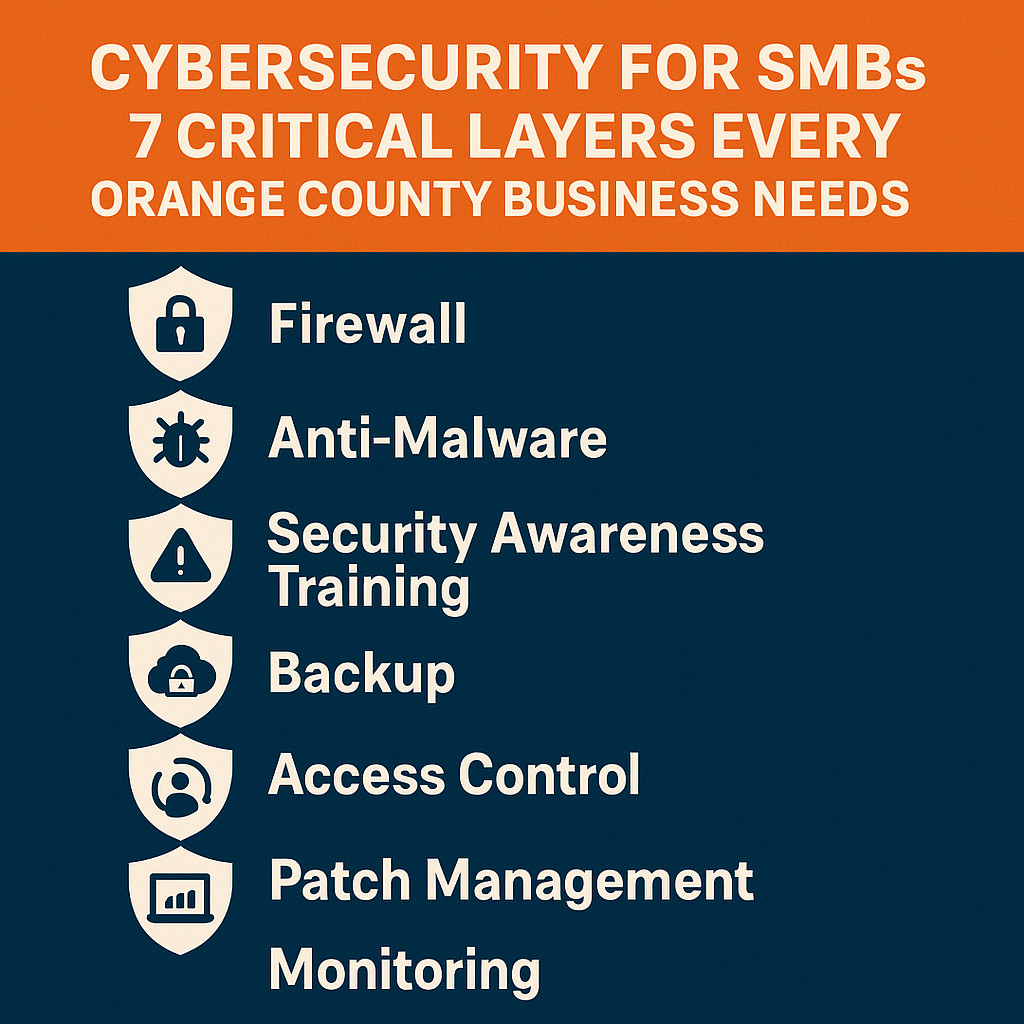
Cybersecurity 2025: 7 Attacks Targeting Small Businesses (and How to Stop Them)
Small businesses face escalating cyber threats in 2025, with attackers specifically targeting companies with limited security infrastructure. From sophisticated phishing campaigns to ransomware attacks, cybercriminals exploit vulnerabilities in outdated systems and untrained staff. This comprehensive guide examines seven critical attack vectors threatening small businesses today and provides actionable strategies to defend against them. Implementing managed cybersecurity services has become essential for protecting sensitive data, maintaining customer trust, and ensuring business continuity in an increasingly dangerous digital landscape. ... Read More