Model Context Protocol (MCP) Explained: The Safer Way to Connect AI to Your Systems
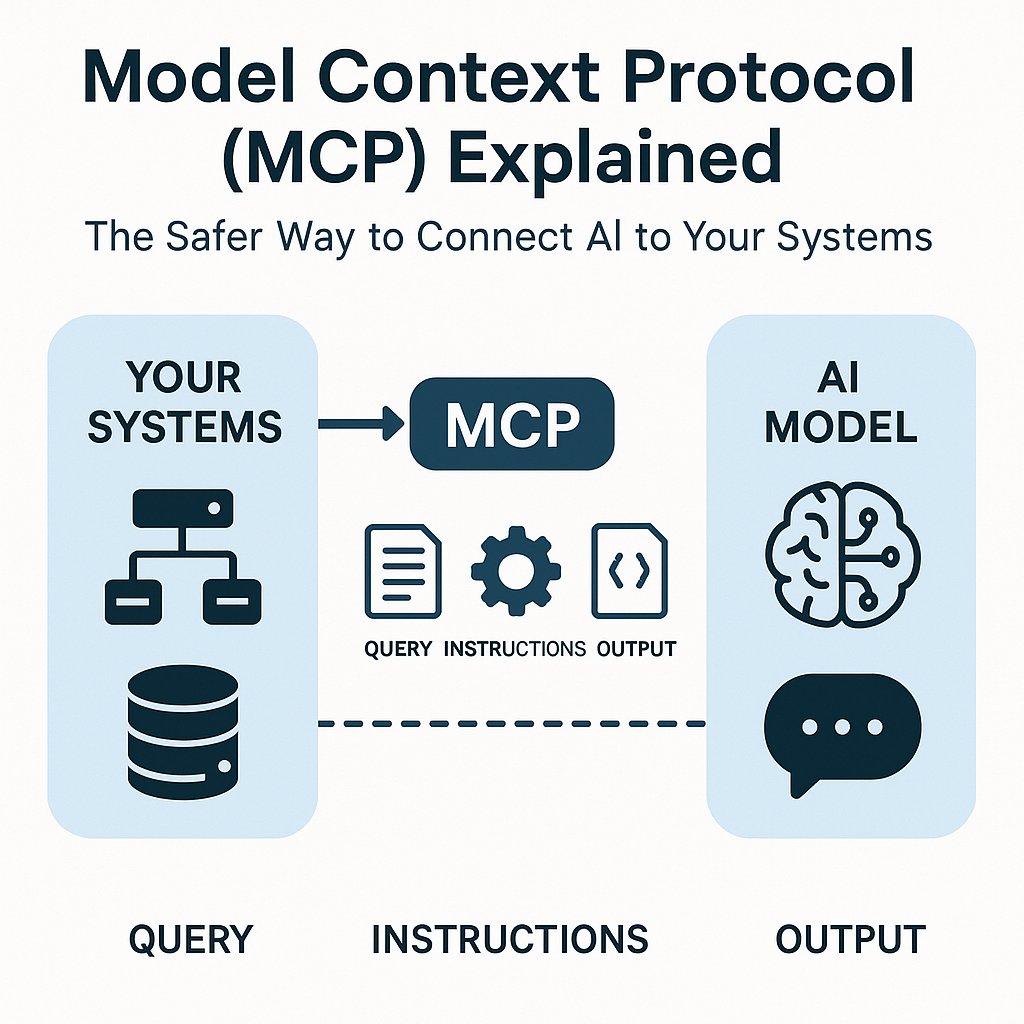
An extensive overview of the security risks associated with integrating Artificial Intelligence (AI) tools—such as ChatGPT and Claude—into business systems, highlighting that this creates a massive, often unsecured, attack surface. It explains the Model Context Protocol (MCP), an open standard designed to standardize these integrations, but stresses that adopting MCP without proper security controls creates “keys to the kingdom” scenarios vulnerable to attacks like prompt injection and token theft. The text then outlines a comprehensive, 12-step security implementation playbook that organizations, particularly Small and Mid-sized Businesses (SMBs), must follow to safely deploy MCP, including mandatory authentication, robust input validation, and continuous security testing. Finally, the document details the services offered by Technijian, an IT provider specializing in secure MCP architecture design and AI security management to help SMBs navigate these complex threats and maintain compliance. ... Read More
