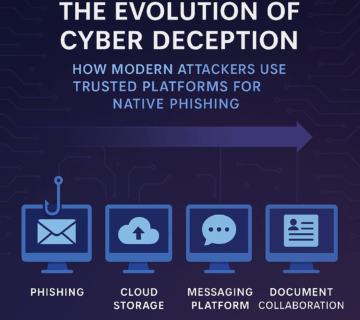
The Evolution of Cyber Deception: How Modern Attackers Use Trusted Platforms for Native Phishing
Native phishing, a sophisticated cyberattack method that exploits legitimate features within trusted enterprise applications like Microsoft OneNote and OneDrive to steal credentials. Unlike traditional phishing, these attacks generate seemingly authentic notifications, bypassing standard security measures and leveraging AI-powered website builders to create convincing fake login portals. The text emphasizes the importance of user awareness training that goes beyond traditional phishing indicators, focuses on behavioral monitoring within collaboration platforms, and advocates for multi-layered defense strategies incorporating robust identity management and integrated security technologies. Finally, the text introduces Technijian, a managed IT services provider offering comprehensive cybersecurity solutions, including advanced threat detection, incident response, and tailored security awareness training to combat evolving threats like native phishing campaigns. ... Read More