Critical Chainlit AI Framework Vulnerabilities Expose Cloud Environments to Security
🎙️ Dive Deeper with Our Podcast!
The artificial intelligence development landscape faced a serious security wake-up call this week as researchers uncovered critical vulnerabilities in Chainlit, one of the most widely adopted open-source frameworks for building conversational AI applications. These security flaws, collectively known as ChainLeak, have exposed enterprise cloud environments to potential data breaches and system compromises, affecting organizations that rely on this popular framework for their AI-powered customer service, internal chatbots, and automated support systems.
Security researchers at Zafran Labs discovered two high-severity vulnerabilities that fundamentally undermine the security architecture of applications built with Chainlit. What makes these discoveries particularly concerning is the framework’s widespread adoption, with approximately 700,000 monthly downloads from the Python Package Index and an estimated 5 million downloads annually. Organizations across healthcare, finance, education, and technology sectors have integrated Chainlit into their production environments, making the potential impact of these vulnerabilities far-reaching.
Understanding the Chainlit Framework and Its Popularity
Chainlit has emerged as a go-to solution for developers building conversational AI applications because it dramatically simplifies the development process. The framework provides developers with pre-built user interface components specifically designed for chat-based interactions, eliminating the need to create custom front-end solutions from scratch. Beyond the visual elements, Chainlit offers robust backend infrastructure that handles the complex plumbing required for production-grade AI applications.
The framework’s built-in authentication systems, session management capabilities, and seamless cloud deployment options have made it particularly attractive to enterprises. Academic institutions have embraced Chainlit for research projects and educational tools, while businesses have deployed it for customer-facing applications that handle sensitive data and critical business processes. This widespread adoption across diverse sectors amplifies the security implications of any vulnerabilities discovered within the framework.
Organizations choose Chainlit because it accelerates time-to-market for AI applications while providing enterprise-grade features that would otherwise require significant development resources. The framework integrates smoothly with popular large language models and vector databases, creating a comprehensive ecosystem for building sophisticated conversational AI systems. Unfortunately, this same widespread adoption means that security vulnerabilities affect a substantial portion of the conversational AI landscape.
CVE-2026-22218: The Arbitrary File Read Vulnerability
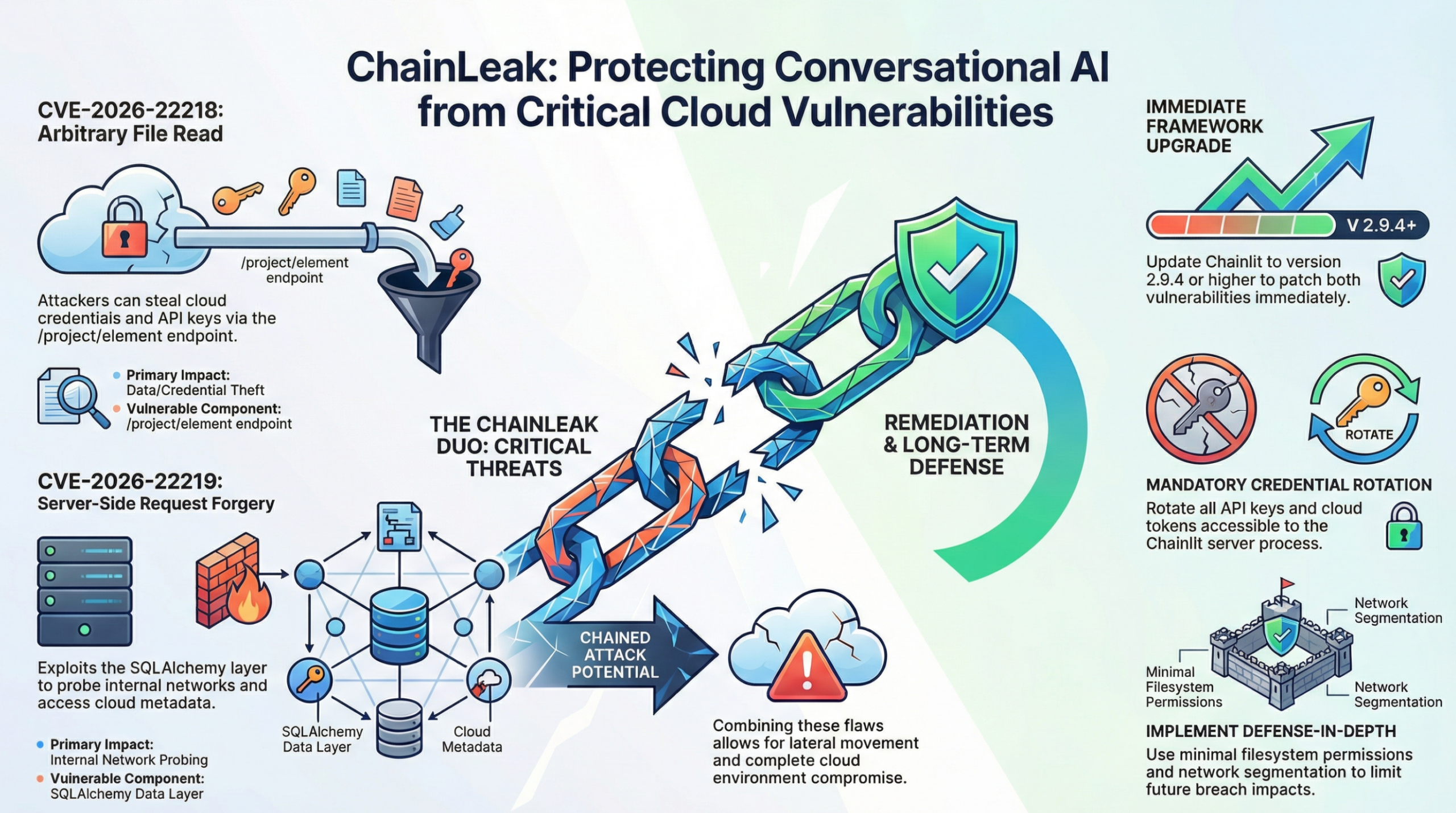
The first vulnerability identified by Zafran Labs researchers carries the designation CVE-2026-22218 and represents an arbitrary file read flaw that attackers can exploit without requiring any user interaction. This vulnerability exists within the project element endpoint, specifically at the path “/project/element,” where Chainlit processes requests for various UI components and data elements.
Attackers exploiting this vulnerability can craft malicious requests containing a custom element with a controlled path field. When Chainlit processes these requests, the framework copies the file located at the attacker-specified path directly into the attacker’s session storage without performing adequate validation or security checks. This fundamental failure in input validation creates a direct pathway for unauthorized file access.
The implications of successful exploitation are severe and far-reaching. Attackers gain the ability to read any file that the Chainlit server process can access, which typically includes configuration files containing database credentials, API keys for third-party services, cloud provider access tokens, application source code, and authentication secrets. In many deployment scenarios, this could include AWS credentials, Azure service principals, Google Cloud service account keys, and other highly sensitive authentication materials.
Organizations storing SQLite databases within their application directories face additional risks, as attackers could extract entire databases containing user information, conversation histories, and proprietary business data. Internal configuration files often reveal network topology, service endpoints, and architectural details that facilitate further attacks. The vulnerability essentially transforms what should be isolated application instances into open books for determined adversaries.
CVE-2026-22219: Server-Side Request Forgery Exploitation
The second vulnerability, tracked as CVE-2026-22219, affects Chainlit deployments that utilize the SQLAlchemy data layer for database operations. This server-side request forgery flaw enables attackers to manipulate the Chainlit server into making unauthorized network requests on their behalf, creating opportunities for internal network reconnaissance and data exfiltration.
Exploitation occurs when attackers submit custom elements with a controlled URL field. The Chainlit server, trusting this input, initiates an outbound GET request to the attacker-specified URL and stores the response data. Attackers can then retrieve this fetched data through element download endpoints, effectively using the Chainlit server as a proxy for accessing resources that should remain inaccessible from external networks.
This vulnerability becomes particularly dangerous in cloud environments where internal services often lack robust authentication because they rely on network segmentation for security. Attackers can probe internal IP address ranges, discover running services, and interact with internal REST APIs that were never designed to face external threats. Cloud metadata services, which provide sensitive information to authorized instances, become accessible through this attack vector.
The server-side request forgery capability allows adversaries to bypass firewalls, access internal documentation, retrieve sensitive data from microservices, and map internal network architecture. Organizations running Chainlit in containerized environments like Kubernetes face additional risks, as attackers might access service discovery endpoints, environment variables, and configuration data that facilitate lateral movement across the infrastructure.
 Combining Vulnerabilities for Maximum Impact
Combining Vulnerabilities for Maximum Impact
Zafran Labs researchers demonstrated that CVE-2026-22218 and CVE-2026-22219 can be chained together in coordinated attacks that achieve complete system compromise. The attack sequence typically begins with exploiting the server-side request forgery vulnerability to map the internal network, identify running services, and locate valuable targets within the cloud environment.
Once attackers understand the internal topology, they leverage the arbitrary file read vulnerability to extract credentials, API keys, and configuration files from the compromised Chainlit server. These stolen credentials often provide access to cloud storage buckets, database servers, and other critical infrastructure components. The combination creates a devastating attack path that transforms a single compromised Chainlit instance into a foothold for broader cloud environment infiltration.
Lateral movement becomes straightforward once attackers possess valid credentials for additional services. Cloud environments built on shared credential models, where multiple services authenticate using common keys or tokens, become particularly vulnerable. Attackers can pivot from the initial Chainlit compromise to databases, storage systems, compute instances, and eventually administrative interfaces that control the entire cloud deployment.
The researchers emphasized that these attack chains require no user interaction, operating entirely through automated exploitation that can be scripted and deployed at scale. Organizations running multiple Chainlit instances face the prospect of coordinated attacks that simultaneously compromise numerous systems, creating complex incident response scenarios that strain security teams and complicate remediation efforts.
Timeline of Discovery and Response
The vulnerability discovery and disclosure process followed a responsible timeline that balanced security concerns with the practical realities of software development. Zafran Labs initially identified the vulnerabilities during routine security research focused on popular AI frameworks and recognized the potential severity immediately.
On November 23, 2025, the research team contacted Chainlit maintainers through established security channels, providing detailed technical descriptions of both vulnerabilities along with proof-of-concept exploits. The initial notification period passed without immediate response, which is common in open-source projects maintained by small teams balancing multiple responsibilities.
The Chainlit team acknowledged receipt of the vulnerability report on December 9, 2025, approximately two weeks after initial contact. This acknowledgment marked the beginning of active remediation efforts as developers analyzed the reported issues, developed fixes, and prepared updated versions of the framework. The development team worked to address both vulnerabilities comprehensively while ensuring that security patches did not introduce breaking changes for existing deployments.
On December 24, 2025, Chainlit released version 2.9.4, which included fixes for both CVE-2026-22218 and CVE-2026-22219. The release notes documented the security improvements without providing exploitation details that could assist attackers. Subsequent releases, including the current version 2.9.6, have built upon these security foundations with additional hardening and validation improvements.
Immediate Actions for Affected Organizations
Organizations running Chainlit in any capacity should treat these vulnerabilities as critical security incidents requiring immediate attention. The first priority involves identifying all Chainlit deployments across development, staging, and production environments. Many organizations discover forgotten or shadow IT instances during this inventory process, highlighting the importance of comprehensive asset management.
Upgrading to Chainlit version 2.9.4 or later represents the minimum acceptable response, though updating to the latest version 2.9.6 provides additional security improvements and bug fixes. The upgrade process should follow standard change management procedures, but expedited timelines are appropriate given the vulnerability severity. Organizations should test upgrades in non-production environments when possible, but production systems should not remain unpatched for extended periods.
While upgrading, security teams should review application logs for suspicious activity patterns that might indicate exploitation attempts. Look for unusual file access patterns, unexpected network connections to internal services, and anomalous element creation requests. The absence of obvious indicators does not guarantee that systems remain uncompromised, as sophisticated attackers often conceal their activities effectively.
Credential rotation becomes essential after patching, particularly for any secrets that might have been accessible through the arbitrary file read vulnerability. This includes API keys, database passwords, cloud provider credentials, and authentication tokens. Organizations should assume that any credential accessible to the Chainlit server process may have been compromised and rotate accordingly.
Long-Term Security Improvements
Beyond immediate patching, organizations should implement defense-in-depth strategies that limit the impact of future vulnerabilities. Running Chainlit instances with minimal filesystem permissions reduces the scope of arbitrary file read attacks, ensuring that application processes can only access files necessary for legitimate operations. Principle of least privilege should guide all permission assignments.
Network segmentation deserves renewed attention, particularly for organizations running Chainlit in cloud environments. Internal services should not rely solely on network isolation for security, instead implementing authentication and authorization controls that assume network perimeters may be breached. Zero-trust architecture principles apply well to AI application deployments.
Regular security assessments, including both automated vulnerability scanning and manual penetration testing, help identify security weaknesses before attackers exploit them. Organizations should include their AI application stack in existing security testing programs, ensuring that Chainlit deployments receive the same scrutiny as traditional web applications and backend services.
Monitoring and logging capabilities provide crucial visibility into application behavior and potential security incidents. Comprehensive logging should capture file access attempts, network connections, authentication events, and element creation requests. Security information and event management systems should ingest these logs and alert on suspicious patterns that might indicate exploitation attempts.
Industry Implications and Broader Context
The ChainLeak vulnerabilities highlight broader security challenges facing the rapidly evolving artificial intelligence application ecosystem. As organizations rush to deploy AI-powered tools and services, security considerations sometimes receive insufficient attention during development and deployment processes. The pressure to innovate quickly can lead to security shortcuts that create long-term vulnerabilities.
Open-source AI frameworks face particular challenges in maintaining security standards. Small maintainer teams often struggle to keep pace with both feature development and security reviews, creating gaps that adversaries can exploit. The AI development community must prioritize security research and vulnerability disclosure programs that help identify and remediate issues before widespread exploitation occurs.
Enterprise adoption of AI frameworks requires corresponding investment in security expertise and processes. Organizations cannot simply deploy AI applications and assume they remain secure without ongoing maintenance, monitoring, and security updates. The same rigorous security practices applied to traditional applications must extend to AI-powered systems.
Frequently Asked Questions
What is Chainlit and why is it so widely used?
Chainlit is an open-source framework that simplifies building conversational AI applications by providing ready-made user interface components, backend infrastructure, and integration tools. Developers appreciate Chainlit because it eliminates the need to build chat interfaces from scratch, includes built-in authentication and session management, and supports easy deployment to cloud platforms. The framework has gained popularity across enterprises, academic institutions, and development teams because it accelerates the creation of production-ready AI applications while handling complex technical requirements automatically.
How serious are these vulnerabilities?
These vulnerabilities are considered high-severity because they allow attackers to read sensitive files and make unauthorized network requests without requiring any user interaction. The arbitrary file read vulnerability can expose API keys, database credentials, cloud provider access tokens, and other critical secrets. The server-side request forgery flaw enables attackers to probe internal networks and access services that should remain isolated. When combined, these vulnerabilities can lead to complete system compromise and lateral movement throughout cloud environments.
Which versions of Chainlit are affected?
All Chainlit versions prior to 2.9.4 contain these vulnerabilities and should be considered insecure. Organizations running any version below 2.9.4 face potential exploitation and should upgrade immediately to version 2.9.4 or later. The current version is 2.9.6, which includes the security fixes along with additional improvements and updates.
Can these vulnerabilities be exploited remotely?
Yes, both vulnerabilities can be exploited remotely without requiring physical access to systems or networks. Attackers only need network connectivity to the Chainlit application, which is particularly concerning for internet-facing deployments. The exploits do not require user interaction, meaning attackers can automate exploitation attempts against multiple targets simultaneously.
What should I do if I suspect my Chainlit deployment was compromised?
Organizations suspecting compromise should immediately isolate affected systems to prevent further lateral movement, begin forensic analysis to determine the scope of the breach, rotate all credentials that might have been accessible through the vulnerabilities, review logs for evidence of exploitation, and engage incident response teams to guide remediation efforts. After addressing immediate concerns, upgrade to the latest Chainlit version and implement additional security controls to prevent future incidents.
Are there temporary mitigations if I cannot upgrade immediately?
While upgrading represents the only complete fix, organizations unable to patch immediately can implement compensating controls such as restricting network access to Chainlit instances using firewalls or VPNs, running Chainlit with minimal filesystem permissions to limit file read scope, implementing additional authentication layers in front of Chainlit applications, monitoring for suspicious file access and network activity, and isolating Chainlit deployments from sensitive internal services. These measures reduce risk but do not eliminate vulnerabilities entirely.
How can I tell if my deployment uses the SQLAlchemy data layer?
Review your Chainlit configuration files and application code to determine whether SQLAlchemy appears in dependency lists or database connection settings. The CVE-2026-22219 server-side request forgery vulnerability specifically affects deployments using SQLAlchemy for data persistence. If you are uncertain about your configuration, assume vulnerability and upgrade to the latest version regardless.
Will upgrading break my existing Chainlit applications?
The Chainlit development team designed version 2.9.4 and subsequent releases to maintain backward compatibility with existing applications, minimizing breaking changes. Most deployments can upgrade without code modifications, though organizations should test upgrades in non-production environments before deploying to production systems. Review the Chainlit release notes for any specific migration steps or compatibility considerations relevant to your deployment.
How Technijian Can Help
Securing your AI infrastructure requires specialized expertise and comprehensive security strategies that address both immediate vulnerabilities and long-term security posture. Technijian provides end-to-end security services specifically designed for organizations deploying artificial intelligence applications and cloud-based systems.
Our security assessment services identify vulnerabilities in your AI application stack, including frameworks like Chainlit, custom-built conversational interfaces, and integrated cloud services. We conduct thorough penetration testing that simulates real-world attack scenarios, helping you discover security weaknesses before malicious actors exploit them. Our team brings deep expertise in both AI technologies and security best practices, ensuring comprehensive evaluation of your systems.
Technijian’s incident response specialists stand ready to assist organizations dealing with potential compromises resulting from the ChainLeak vulnerabilities or other security incidents. We provide rapid forensic analysis, containment strategies, and remediation guidance that minimizes business impact while thoroughly addressing security concerns. Our experience with cloud security incidents enables efficient response that balances security requirements with operational continuity.
Beyond immediate security concerns, Technijian helps organizations build robust security foundations for their AI initiatives. We design and implement defense-in-depth architectures that protect AI applications through multiple security layers, develop security monitoring and alerting systems tailored to AI workloads, establish secure development lifecycle practices for AI projects, and provide ongoing security management services that keep your systems protected as threats evolve.
Our cloud security expertise ensures that your Chainlit deployments and other AI applications benefit from proper network segmentation, least-privilege access controls, comprehensive logging and monitoring, and automated security compliance validation. We help organizations implement zero-trust architectures that assume breach scenarios and limit potential damage through strategic security controls.
Technijian also offers security training programs that equip your development and operations teams with the knowledge needed to build and maintain secure AI applications. We provide hands-on workshops covering secure coding practices for AI frameworks, cloud security fundamentals, vulnerability assessment techniques, and incident response procedures. Empowering your teams with security expertise creates lasting organizational capabilities that extend beyond individual projects.
Contact Technijian today to schedule a comprehensive security assessment of your AI infrastructure and develop a customized security strategy that protects your organization from emerging threats while enabling continued innovation. Our team is ready to help you navigate the complex security landscape of modern AI applications and build resilient systems that withstand evolving attack techniques.
About Technijian
Technijian is a premier managed IT services provider in Irvine, specializing in delivering secure, scalable, and innovative AI, SEO, and technology solutions across Orange County and Southern California. Founded in 2000 by Ravi Jain, what started as a one-man IT shop has evolved into a trusted technology partner with teams of engineers, AI specialists, cybersecurity professionals, and digital marketing experts both in the U.S. and internationally.
Headquartered in Irvine, we provide comprehensive cybersecurity solutions, IT support, AI implementation services, cloud services, and search engine optimization (SEO) and digital visibility solutions throughout Orange County—from Aliso Viejo, Anaheim, Costa Mesa, and Fountain Valley to Newport Beach, Santa Ana, Tustin, and beyond. Our extensive experience with enterprise telecommunications and security deployments, combined with our expertise in SEO-driven growth strategies and our deep understanding of local business needs, makes us the ideal partner for organizations seeking solutions that deliver real protection, online visibility, and operational efficiency.
We work closely with clients across diverse industries, including healthcare, finance, law, retail, and professional services, to design integrated technology and SEO strategies that reduce risk, enhance productivity, improve search rankings, and strengthen digital presence while maintaining the highest protection standards. Our Irvine-based office remains our primary hub, delivering the personalized service and responsive support that businesses across Orange County have relied on for over two decades.
With expertise spanning cybersecurity, managed IT services, telecommunications, AI implementation, SEO and digital marketing, consulting, and cloud solutions, Technijian has become the go-to partner for small to medium businesses seeking reliable technology infrastructure and measurable online growth. Whether you need 3CX deployment in Irvine, telecommunications optimization in Santa Ana, IT consulting in Anaheim, or SEO services to increase visibility and lead generation, we deliver solutions that align with your business goals and operational requirements.
Partner with Technijian and experience the difference of a local IT company that combines global technology expertise, SEO-driven growth, and community-focused service. Our mission is to help businesses across Irvine, Orange County, and Southern California harness the power of advanced technology and digital marketing to stay protected, visible, efficient, and competitive in today’s digital world.