Sneaky2FA PhaaS Kit Now Uses Red Teamers’ Browser-in-the-Browser Attack
🎙️ Dive Deeper with Our Podcast!
Sneaky2FA Phishing and Browser-in-the-Browser Attacks
The cybersecurity landscape continues to evolve with increasingly sophisticated threats, and the latest development in phishing attacks demonstrates just how creative cybercriminals have become. The Sneaky2FA phishing-as-a-service platform has recently incorporated browser-in-the-browser (BitB) capabilities into its arsenal, marking a significant escalation in the ongoing battle to protect Microsoft 365 credentials and user sessions.
This development represents a troubling trend where threat actors are adopting techniques originally designed by security researchers to test organizational defenses. As businesses increasingly rely on cloud-based services and multi-factor authentication for security, attackers are developing more convincing methods to circumvent these protections.
Understanding Phishing-as-a-Service Platforms
Phishing-as-a-service platforms have transformed the cybercrime ecosystem by lowering the barrier to entry for conducting sophisticated attacks. These platforms operate similarly to legitimate software-as-a-service offerings, providing would-be attackers with ready-made tools, infrastructure, and support to launch phishing campaigns without requiring extensive technical knowledge.
Sneaky2FA currently stands among the most widely deployed PhaaS platforms, sharing the spotlight with Tycoon2FA and Mamba2FA. These services primarily target Microsoft 365 accounts, which have become attractive targets due to their widespread use in corporate environments and the valuable data they contain. The platform previously gained notoriety for its SVG-based attacks and attacker-in-the-middle tactics, where the authentication process is proxied to the legitimate service through a phishing page that captures and relays valid session tokens directly to attackers.
The business model behind these platforms is particularly concerning. Cybercriminals can subscribe to these services, often paying monthly fees, and gain access to constantly updated phishing kits that incorporate the latest evasion techniques and social engineering tactics. This commoditization of cybercrime has led to a proliferation of phishing attacks across organizations of all sizes.
The Browser-in-the-Browser Technique Explained
The browser-in-the-browser attack technique was originally developed by security researcher mr.d0x in 2022 as a demonstration of how convincingly fake authentication windows could be created. Since its introduction, threat actors have rapidly adopted this method for real-world attacks targeting various platforms, including Facebook and Steam accounts.
The technique works by creating an extremely convincing fake browser pop-up window within a webpage. When users land on an attacker-controlled site, they encounter what appears to be a legitimate OAuth authentication window complete with a URL bar displaying the official domain of the targeted service. However, this entire window is actually an iframe element styled to mimic a genuine browser pop-up with remarkable accuracy.
The template for these fake pop-ups can be customized with specific URLs and window titles, making them virtually indistinguishable from legitimate authentication prompts to the untrained eye. The deception is particularly effective because users have been trained to look for HTTPS connections and official domain names in the address bar as indicators of legitimacy. When these elements are convincingly spoofed within a fake window, users naturally trust what they see.
How Sneaky2FA Implements the Attack
The attack chain starts when a target is sent a phishing link that takes them to a domain hosted on previewdoc[.]com, usually via email or messaging services. Upon clicking the link, victims encounter a Cloudflare Turnstile bot check, which adds an additional layer of perceived legitimacy to the operation. After passing this check, users are presented with a prompt to sign in with their Microsoft account to view a purported document.
When victims click the “Sign in with Microsoft” option, the fake BitB window renders on their screen. The sophistication of this implementation is evident in its attention to detail. The fake window automatically adjusts its appearance based on the victim’s operating system and browser, displaying appropriate styling for Edge on Windows or Safari on macOS. This dynamic adaptation makes the phishing attempt even more convincing, as users see an interface that matches their familiar environment.
Inside the fake pop-up window, Sneaky2FA loads its reverse-proxy Microsoft phishing page. This setup leverages the actual Microsoft login flow, meaning users interact with what appears to be a genuine authentication process. However, the attacker-in-the-middle system captures both the account credentials entered by the victim and the session token generated upon successful authentication. This dual capture is particularly dangerous because it allows attackers to bypass two-factor authentication protections that many organizations rely on for security.
The BitB technique essentially serves as a cosmetic deception layer on top of Sneaky2FA’s existing attacker-in-the-middle capabilities. While the underlying credential theft mechanism remains the same, the addition of the fake browser window significantly enhances the realism of the attack chain and increases the likelihood of victim compliance.
Advanced Evasion Techniques
Beyond the visual deception of the fake browser window, Sneaky2FA incorporates numerous technical measures designed to evade detection by security tools and researchers. The phishing kit employs conditional loading that directs automated scanners and security researchers to benign pages while serving the actual phishing content only to potential victims. This selective presentation makes it difficult for security teams to analyze the threat and develop appropriate countermeasures.
The HTML and JavaScript code underlying Sneaky2FA pages features heavy obfuscation designed to defeat static detection and pattern-matching systems. These obfuscation techniques include breaking up user interface text with invisible HTML tags, embedding background and interface elements as encoded images rather than text, and implementing other modifications that remain invisible to users but significantly complicate automated analysis.
These pages are specifically crafted with evasion in mind, and according to security researchers, they are unlikely to trigger warnings when visited by users. This means that even organizations with URL filtering and web content scanning solutions may struggle to identify and block these phishing sites before users encounter them. The constant evolution of these evasion techniques represents an ongoing arms race between attackers and security defenders.
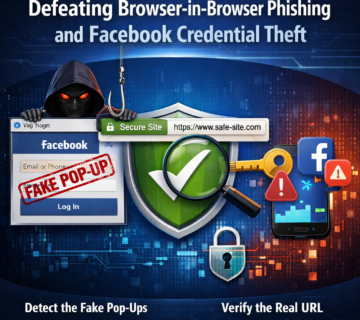
Identifying and Protecting Against BitB Attacks
While browser-in-the-browser attacks are sophisticated, there are several methods users can employ to identify fake pop-up windows. One of the most reliable techniques involves attempting to drag the login window outside the boundaries of the original browser window. Legitimate pop-up windows can be moved anywhere on the screen, while iframe-based fake windows cannot be moved beyond the parent browser window because they are embedded elements of the webpage itself.
Another telltale sign involves checking the operating system taskbar. Authentic browser pop-ups appear as separate browser instances in the taskbar, allowing users to minimize, maximize, or close them independently. Fake pop-ups created using the BitB technique do not appear in the taskbar because they are not separate windows but rather elements embedded within the main browser window.
Organizations should implement comprehensive security awareness training that specifically addresses these newer phishing techniques. Employees need to understand not only traditional phishing indicators but also the more sophisticated deception tactics employed by modern threat actors. Regular simulated phishing exercises that incorporate BitB-style attacks can help employees develop the skepticism and verification habits necessary to recognize these threats.
The Broader Phishing-as-a-Service Threat Landscape
The support for BitB capabilities has appeared in other phishing-as-a-service platforms beyond Sneaky2FA. Raccoon0365, also known as Storm-2246, recently incorporated similar functionality before being disrupted through a coordinated effort by Microsoft and Cloudflare. That operation successfully prevented the theft of thousands of Microsoft 365 credentials, but it also highlighted the scale at which these platforms operate.
The disruption of individual phishing platforms, while beneficial, represents only a temporary setback for the broader phishing-as-a-service ecosystem. When one platform is taken down, others quickly emerge to fill the void, often incorporating lessons learned from the failures of their predecessors. This resilience makes the phishing-as-a-service model particularly challenging for law enforcement and security organizations to combat effectively.
The continuous innovation within these platforms demonstrates that cybercriminals are actively monitoring security research and rapidly integrating new techniques into their tools. The adoption of mr.d0x’s BitB technique by multiple phishing platforms within a relatively short timeframe illustrates how quickly theoretical attack methods can become operational threats.
Technical Defense Strategies
Organizations need to implement layered security controls that address both the technical and human elements of these attacks. Email security solutions should incorporate advanced threat detection capabilities that can identify suspicious links and attachments, including those hosted on legitimate-seeming infrastructure like previewdoc[.]com. However, relying solely on automated detection is insufficient given the sophisticated evasion techniques employed by modern phishing kits.
Although multi-factor authentication is still an essential security measure, businesses need to be aware that standard MFA setups can be circumvented via session token theft. Implementing conditional access policies that evaluate device compliance, location, and other contextual factors can help detect and prevent unauthorized access even when valid credentials and session tokens have been compromised. Organizations should also consider implementing session token binding and refresh token rotation to limit the window of opportunity for attackers using stolen credentials.
Network monitoring and anomaly detection play important roles in identifying successful compromises. Unusual authentication patterns, such as simultaneous logins from geographically distant locations or access attempts during unusual hours, can indicate compromised accounts. Security teams should establish baseline normal behavior for user accounts and investigate deviations that could signal unauthorized access.
Frequently Asked Questions
What makes the browser-in-the-browser attack so effective?
The browser-in-the-browser attack succeeds because it exploits users’ learned trust behaviors. People have been trained to verify the URL in the address bar and look for HTTPS indicators as signs of legitimacy. When these elements are convincingly spoofed within a fake window, users naturally trust what they see. The fake window appears virtually identical to legitimate authentication pop-ups, complete with the correct branding, URL, and security indicators.
Can two-factor authentication protect against Sneaky2FA attacks?
Unfortunately, traditional two-factor authentication does not provide complete protection against Sneaky2FA attacks. Because the platform uses attacker-in-the-middle techniques, it captures not only your username and password but also the session token generated after successful authentication, including completion of two-factor verification. This allows attackers to authenticate to your account even though 2FA is enabled. However, advanced authentication methods that include device binding or behavioral analysis may provide additional protection.
How can I tell if a login window is fake?
There are several methods to identify fake login windows. Try dragging the window beyond the borders of your browser window. If it cannot be moved outside the browser boundaries, it is likely a fake iframe-based window. Additionally, check your taskbar to see if the pop-up appears as a separate browser instance. Legitimate pop-ups will appear in your taskbar, while fake windows will not. When in doubt, close the window and navigate directly to the service by typing the URL into your browser rather than clicking links.
What should I do if I suspect I have fallen victim to a phishing attack?
If you believe you have entered credentials into a phishing site, act immediately. Change your password from a different device or browser that you know is secure. Enable or update your two-factor authentication settings. Contact your IT security team right away so they can monitor your account for suspicious activity and take additional protective measures. Review recent account activity for any unauthorized access or changes. The faster you respond, the better chance you have of preventing significant damage.
Why are Microsoft 365 accounts such popular targets for these attacks?
Microsoft 365 accounts represent highly valuable targets because they typically provide access to extensive corporate data, including emails, documents, contacts, and calendar information. A compromised Microsoft 365 account can give attackers entry points into broader organizational networks and systems. Additionally, the widespread adoption of Microsoft 365 across organizations of all sizes means that phishing campaigns targeting these accounts have a broad potential victim base. The integration of Microsoft 365 with other business applications also makes these accounts particularly valuable for lateral movement within compromised networks.
How often should organizations conduct security awareness training?
Security awareness training should be an ongoing process rather than a one-time event. Organizations should conduct formal training sessions at least quarterly, with monthly or even weekly security tips and reminders. Regular simulated phishing exercises help reinforce training concepts and identify employees who may need additional support. Training content should be updated continuously to reflect emerging threats like browser-in-the-browser attacks. The most effective programs combine formal training sessions with real-time coaching and feedback based on simulated phishing results.
How Technijian Can Help
At Technijian, we understand that protecting your organization from sophisticated phishing attacks requires a comprehensive approach that combines advanced technology, proactive monitoring, and ongoing education. Our cybersecurity experts stay current with emerging threats like the Sneaky2FA platform and browser-in-the-browser attacks, ensuring your defenses evolve alongside the threat landscape.
Our managed security services include implementation and management of advanced email security solutions that detect and block phishing attempts before they reach your users. We deploy multi-layered authentication strategies that go beyond basic two-factor authentication, incorporating conditional access policies, device compliance checks, and anomaly detection to identify potential compromises even when credentials have been stolen.
Technijian provides comprehensive security awareness training programs tailored to your organization’s specific risks and industry requirements. Our training includes simulated phishing exercises that incorporate the latest attack techniques, giving your employees practical experience identifying sophisticated threats like BitB attacks. We provide detailed reporting on training effectiveness and offer targeted coaching for employees who may need additional support.
Our security operations center monitors your environment around the clock for indicators of compromise, including unusual authentication patterns, suspicious session activity, and other anomalies that could signal a successful phishing attack. When threats are detected, our team responds immediately to contain the incident and prevent further damage.
We also conduct regular security assessments to identify vulnerabilities in your authentication infrastructure and implement technical controls that make it harder for attackers to succeed even if users accidentally provide credentials to phishing sites. Our experts can help you implement session token protections, enforce device compliance requirements, and establish baseline normal behavior patterns for your user accounts.
Don’t wait until your organization becomes another victim of increasingly sophisticated phishing attacks. Contact Technijian today to schedule a comprehensive security assessment and learn how our managed cybersecurity services can protect your Microsoft 365 environment and other critical business systems from evolving threats. Our team of experienced professionals is ready to help you build robust defenses that keep your data and accounts secure.
About Technijian
Technijian is a premier Managed IT Services provider in Irvine, specializing in delivering secure, scalable, and innovative AI and technology solutions across Orange County and Southern California. Founded in 2000 by Ravi Jain, what started as a one-man IT shop has evolved into a trusted technology partner with teams of engineers, AI specialists, and cybersecurity professionals both in the U.S. and internationally.
Headquartered in Irvine, we provide comprehensive cybersecurity solutions, IT support, AI implementation services, and cloud services throughout Orange County—from Aliso Viejo, Anaheim, Costa Mesa, and Fountain Valley to Newport Beach, Santa Ana, Tustin, and beyond. Our extensive experience with enterprise security deployments, combined with our deep understanding of local business needs, makes us the ideal partner for organizations seeking to implement security solutions that provide real protection.
We work closely with clients across diverse industries, including healthcare, finance, law, retail, and professional services, to design security strategies that reduce risk, enhance productivity, and maintain the highest protection standards. Our Irvine-based office remains our primary hub, delivering the personalized service and responsive support that businesses across Orange County have relied on for over two decades.
With expertise spanning cybersecurity, managed IT services, AI implementation, consulting, and cloud solutions, Technijian has become the go-to partner for small to medium businesses seeking reliable technology infrastructure and comprehensive security capabilities. Whether you need Cisco Umbrella deployment in Irvine, DNS security implementation in Santa Ana, or phishing prevention consulting in Anaheim, we deliver technology solutions that align with your business goals and security requirements.
Partner with Technijian and experience the difference of a local IT company that combines global security expertise with community-driven service. Our mission is to help businesses across Irvine, Orange County, and Southern California harness the power of advanced cybersecurity to stay protected, efficient, and competitive in today’s threat-filled digital world.