Okta SSO Accounts Under Siege: New Vishing Attacks Expose Security Gaps
🎙️ Dive Deeper with Our Podcast!
Cybercriminals have evolved their tactics once again, and this time they’re combining old-school phone scams with cutting-edge technology to breach enterprise security systems. Organizations using Okta’s single sign-on platform are facing a sophisticated wave of voice-based phishing attacks that bypass traditional security measures and grant hackers access to sensitive corporate data.
These attacks represent a troubling shift in how cybercriminals operate, leveraging human psychology and real-time technical manipulation to defeat even the most advanced authentication systems.
What Makes These Vishing Attacks Different
Voice phishing, commonly known as vishing, has been around for years. However, the latest generation of attacks targeting Okta users employs specialized phishing kits designed specifically for live phone interactions. These aren’t your typical static fake websites that sit idle waiting for victims to stumble upon them.
Instead, attackers use sophisticated command-and-control panels that allow them to manipulate phishing pages in real time during active phone calls. When a victim enters their credentials, those details immediately flow to the attacker’s backend systems, often through encrypted Telegram channels. The attacker can then trigger genuine authentication attempts while still speaking with the target on the phone.
This synchronization creates a seamless illusion of legitimacy. When multi-factor authentication challenges appear on both the real service and the fake phishing page simultaneously, victims have little reason to suspect anything is wrong.
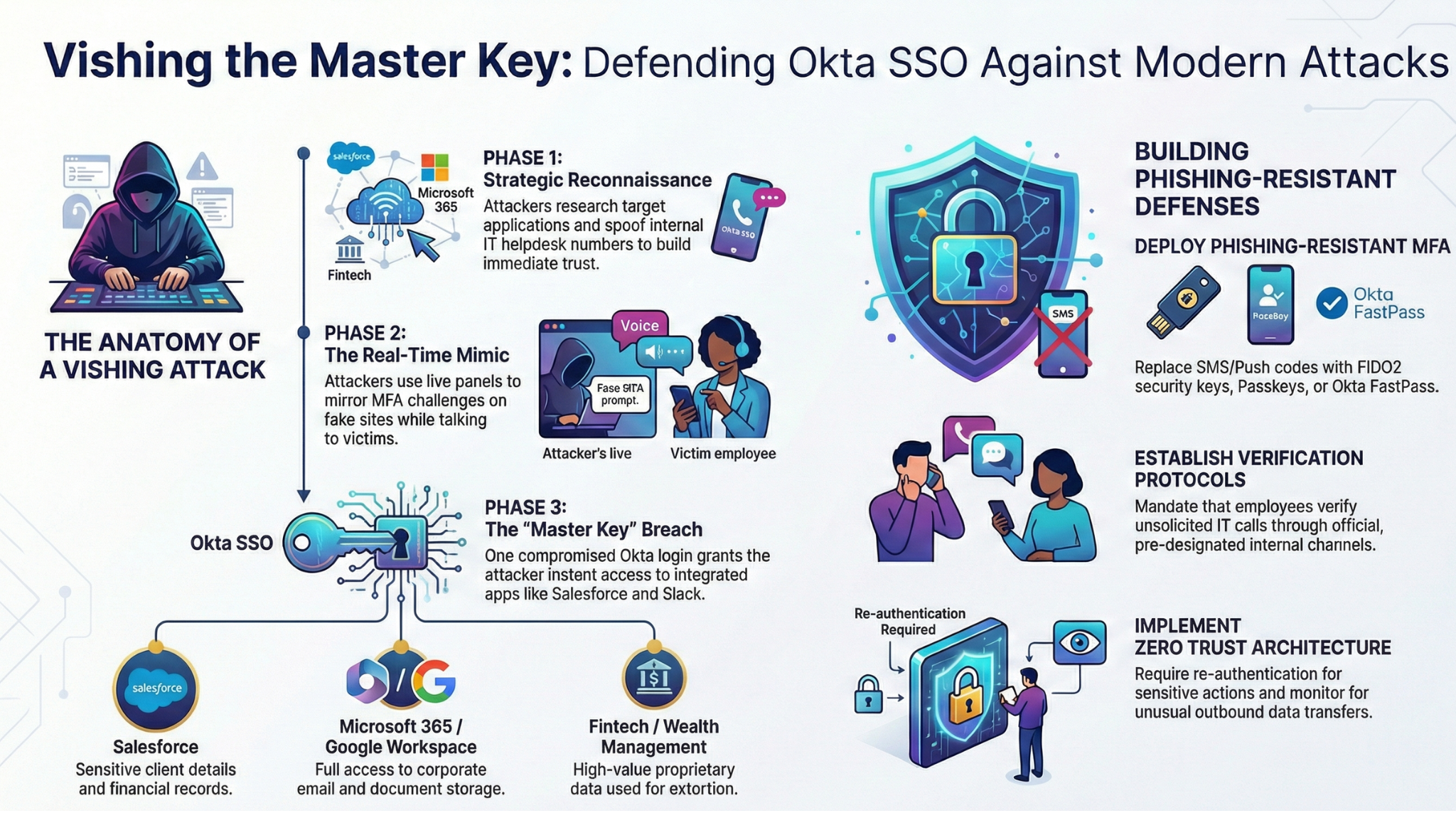
The Anatomy of an Okta SSO Vishing Campaign
Knowing how these attacks work makes it easier to see why they work so well. Threat actors don’t just pick up the phone and start calling random employees. These campaigns involve careful planning and reconnaissance.
Initial Research Phase
Before making contact, attackers gather intelligence on their targets. They identify which applications employees use, locate phone numbers associated with company IT support teams, and profile specific individuals who might have access to valuable systems. This groundwork makes their impersonation far more convincing.
The Social Engineering Call
Armed with inside knowledge, attackers place calls to employees using spoofed numbers that appear to come from legitimate corporate helpdesks or IT departments. They offer assistance with setting up new security features, such as passkeys for Okta authentication. The premise sounds reasonable, especially if the employee has recently heard about security updates from their actual IT team.
During these conversations, attackers direct victims to visit fraudulent websites designed to mimic internal company portals. These sites often incorporate the company name along with terms like “internal” or “my” to appear authentic. A targeted employee at a company called Acme Corp might be directed to acmeinternal[.]com or myacme[.]com.
Real-Time Credential Harvesting
Once the victim begins entering their username and password on the phishing site, those credentials transmit instantly to the attacker’s control panel. The attacker then attempts to log into the actual Okta service while maintaining the phone conversation. When the legitimate system prompts for multi-factor authentication, the attacker updates the phishing page to display a matching prompt.
This coordination defeats even number-matching push notifications, which were specifically designed to prevent man-in-the-middle attacks. The attacker simply tells the victim which number to select, and the phishing kit displays the corresponding challenge in the browser.
Why Okta SSO Is Such a Valuable Target
Okta functions as a centralized gateway to enterprise applications. Once authenticated through Okta’s single sign-on service, employees gain seamless access to dozens of critical business platforms without needing to log in again.
Common integrations include Microsoft 365, Google Workspace, Salesforce, Slack, Dropbox, Zoom, Atlassian products, and many other essential business tools. An employee’s Okta dashboard essentially provides a menu of every application they’re authorized to use.
For cybercriminals, compromising a single Okta account is like obtaining a master key. They can browse the victim’s dashboard, identify which platforms contain the most valuable information, and proceed to exfiltrate data from multiple sources using just one set of stolen credentials.
Security researchers have observed attackers showing particular interest in Salesforce after gaining Okta access, noting its ease of data extraction. Customer relationship management platforms like Salesforce contain highly sensitive information including client details, financial records, and proprietary business intelligence.
 The Extortion Endgame
The Extortion Endgame
These attacks don’t end with simple data theft. Once cybercriminals detect that their unauthorized access has been discovered or terminated, they immediately pivot to extortion. Victims receive threatening emails demanding payment to prevent the publication of stolen data.
Several of these extortion demands have reportedly been signed by ShinyHunters, a notorious threat group responsible for numerous high-profile data breaches. While the group has declined to confirm their involvement in these specific Okta-targeting campaigns, the connection suggests these attacks may be part of a broader, organized criminal operation.
Current intelligence indicates that threat actors are actively focusing on companies in fintech, wealth management, financial services, and advisory sectors, where the data holds particularly high value.
Defensive Measures Organizations Must Implement
Traditional multi-factor authentication clearly isn’t enough to stop these sophisticated vishing attacks. Organizations need to adopt phishing-resistant authentication methods that can’t be defeated through social engineering.
Deploy Phishing-Resistant MFA
Okta recommends implementing authentication systems that are inherently resistant to interception. Options include:
- Okta FastPass: A passwordless authentication method that uses device-bound passkeys
- FIDO2 Security Keys: Physical hardware tokens that provide cryptographic proof of identity
- Passkeys: Cryptographic credentials tied to specific devices and services
These technologies rely on public key cryptography rather than transmittable codes, making them immune to phishing attacks regardless of how convincing the social engineering might be.
Employee Training and Awareness
Technical solutions alone won’t stop determined attackers. Organizations must invest in comprehensive security awareness training that specifically addresses vishing tactics. Employees should understand that:
- Legitimate IT staff rarely initiate unsolicited calls requesting credential verification
- Official support channels should be used to verify unexpected security requests
- No legitimate service will ask employees to enter credentials on websites accessed through links provided during phone calls
- Urgency and pressure are common manipulation tactics
Regular simulated phishing and vishing exercises help reinforce these concepts and identify employees who may need additional training.
Implement Zero Trust Architecture
Adopting zero trust principles limits the damage attackers can cause even if they compromise an account. This includes:
- Requiring re-authentication for sensitive actions
- Implementing just-in-time access provisioning
- Monitoring for unusual access patterns and data exfiltration
- Segmenting systems to prevent lateral movement
Establish Verification Protocols
Create clear procedures for employees to verify unexpected IT support interactions. These might include:
- Designated callback numbers for confirming IT support requests
- Secondary communication channels for validation
- Mandatory waiting periods before implementing significant security changes
- Approval requirements for authentication method modifications
Detecting Active Vishing Campaigns
Security teams should monitor for indicators that suggest ongoing vishing attempts targeting their organization:
- Reports from employees about suspicious IT support calls
- Unusual spikes in failed authentication attempts
- Authentication attempts from unexpected geographic locations
- Phishing domains registered that incorporate company names
- Suspicious outbound data transfers following successful authentications
Establishing clear reporting channels and encouraging employees to report suspicious contacts without fear of criticism creates early warning opportunities.
The Broader Threat Landscape
These Okta-targeting vishing campaigns represent part of a larger trend toward hybrid attacks that combine social engineering with sophisticated technical capabilities. Cybercriminals recognize that human psychology remains the weakest link in even the most advanced security architectures.
The “as a service” model for these phishing kits lowers the barrier to entry for less technical criminals. Groups that might lack the skills to develop custom attack infrastructure can now purchase ready-made solutions complete with real-time control panels and credential harvesting capabilities.
This democratization of advanced hacking tools means organizations can no longer assume they’re too small or obscure to be targeted. Any company using popular identity providers like Okta, Microsoft, or Google becomes a potential victim.
Frequently Asked Questions
What is vishing and how does it differ from regular phishing?
Vishing combines voice calls with phishing techniques. While traditional phishing relies on emails or text messages to direct victims to fraudulent websites, vishing involves direct phone conversations where attackers impersonate trusted figures like IT support staff. This personal interaction makes the deception more convincing and allows attackers to manipulate victims in real time.
Can multi-factor authentication really be bypassed?
Standard MFA methods like SMS codes, authenticator app codes, and even push notifications can be defeated through sophisticated adversary-in-the-middle attacks. When attackers control both the phone conversation and a real-time phishing page, they can intercept these codes as victims enter them. Only phishing-resistant methods like FIDO2 security keys and passkeys are immune to these attacks.
How can employees verify if an IT support call is legitimate?
Employees should never provide credentials or access sensitive systems based solely on an incoming call. Instead, they should hang up and contact their IT department through official channels listed on the company intranet or directory. If the call was legitimate, IT will have a record of the outreach. This simple verification step stops most vishing attacks.
How should I respond if I think I’ve been singled out?
Immediately report the incident to your security team, even if you didn’t provide any information. Change your passwords using a known-good device and connection, not the one potentially compromised. Review recent account activity for unauthorized access. Your security team can then investigate whether credentials were compromised and take appropriate containment measures.
Why are financial services companies being targeted?
Financial services, fintech, and wealth management firms handle extremely valuable data including client financial information, investment strategies, and personally identifiable information. This data commands high prices on criminal marketplaces and provides excellent leverage for extortion. Additionally, these sectors often have complex ecosystems of connected applications, making SSO compromises particularly damaging.
Are small companies at risk or just large enterprises?
Any organization using Okta or similar SSO platforms is a potential target. While large enterprises may seem like more obvious targets, small and medium-sized businesses often have weaker security postures and may be viewed as easier victims. The “as a service” phishing kits make it economical for criminals to target organizations of any size.
How quickly do attackers act after stealing credentials?
Attackers typically move immediately. During active vishing campaigns, credential theft and initial account access occur while the attacker is still on the phone with the victim. Data exfiltration often begins within minutes of gaining access. This speed emphasizes the need for real-time security monitoring and rapid incident response capabilities.
What data are attackers most interested in stealing?
Priority targets include customer databases, financial records, intellectual property, authentication credentials, business intelligence, and any information that could be used for further attacks or sold to competitors. Platforms like Salesforce are particularly attractive because they aggregate large amounts of sensitive business information in easily exportable formats.
How Technijian Can Help
Defending against sophisticated vishing attacks requires comprehensive security expertise and proactive defense strategies. Technijian specializes in helping organizations strengthen their identity and access management posture against evolving threats.
Our cybersecurity team can assess your current authentication infrastructure and identify vulnerabilities that vishing attacks might exploit. We’ll work with you to implement phishing-resistant MFA solutions including FIDO2 security keys, passkeys, and advanced authentication systems that can’t be defeated through social engineering.
Beyond technical implementations, Technijian provides customized security awareness training that specifically addresses vishing tactics. Our programs use realistic simulations to help employees recognize and resist social engineering attempts, creating a human firewall that complements your technical defenses.
We also offer managed security services that provide continuous monitoring for suspicious authentication patterns, potential credential compromise, and early indicators of vishing campaigns targeting your organization. Our security operations center can detect and respond to threats before attackers successfully exfiltrate sensitive data.
For organizations already using Okta or considering identity provider solutions, Technijian provides architecture consulting to ensure your SSO implementation follows security best practices and incorporates appropriate controls to limit the blast radius of potential compromises.
Don’t wait until your organization becomes the next vishing victim. Contact Technijian today to schedule a comprehensive security assessment and learn how we can help protect your critical systems and data from these sophisticated social engineering attacks. Our team is ready to help you build resilient defenses that protect against both current threats and emerging attack techniques.
About Technijian
Technijian is a premier managed IT services provider in Irvine, specializing in delivering secure, scalable, and innovative AI, SEO, and technology solutions across Orange County and Southern California. Founded in 2000 by Ravi Jain, what started as a one-man IT shop has evolved into a trusted technology partner with teams of engineers, AI specialists, cybersecurity professionals, and digital marketing experts both in the U.S. and internationally.
Headquartered in Irvine, we provide comprehensive cybersecurity solutions, IT support, AI implementation services, cloud services, and search engine optimization (SEO) and digital visibility solutions throughout Orange County—from Aliso Viejo, Anaheim, Costa Mesa, and Fountain Valley to Newport Beach, Santa Ana, Tustin, and beyond. Our extensive experience with enterprise telecommunications and security deployments, combined with our expertise in SEO-driven growth strategies and our deep understanding of local business needs, makes us the ideal partner for organizations seeking solutions that deliver real protection, online visibility, and operational efficiency.
We work closely with clients across diverse industries, including healthcare, finance, law, retail, and professional services, to design integrated technology and SEO strategies that reduce risk, enhance productivity, improve search rankings, and strengthen digital presence while maintaining the highest protection standards. Our Irvine-based office remains our primary hub, delivering the personalized service and responsive support that businesses across Orange County have relied on for over two decades.
With expertise spanning cybersecurity, managed IT services, telecommunications, AI implementation, SEO and digital marketing, consulting, and cloud solutions, Technijian has become the go-to partner for small to medium businesses seeking reliable technology infrastructure and measurable online growth. Whether you need 3CX deployment in Irvine, telecommunications optimization in Santa Ana, IT consulting in Anaheim, or SEO services to increase visibility and lead generation, we deliver solutions that align with your business goals and operational requirements.
Partner with Technijian and experience the difference of a local IT company that combines global technology expertise, SEO-driven growth, and community-focused service. Our mission is to help businesses across Irvine, Orange County, and Southern California harness the power of advanced technology and digital marketing to stay protected, visible, efficient, and competitive in today’s digital world.





