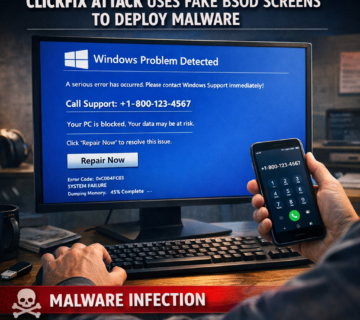
ClickFix Attack Uses Fake BSOD Screens to Deploy Malware
A sophisticated social engineering campaign known as ClickFix, which targets employees in the hospitality industry by mimicking legitimate Booking.com communications. The attack leverages fake Blue Screen of Death (BSOD) errors to manipulate panicked users into executing malicious PowerShell scripts. Once the victim follows the deceptive instructions, a remote access trojan called DCRAT is installed, granting hackers total control over the infected system and its sensitive data. Because these threats utilize legitimate system tools to evade detection, the source emphasizes the necessity of specialized cybersecurity training and advanced monitoring. Ultimately, the report highlights how modern cybercriminals exploit psychological pressure and industry-specific workflows to bypass traditional security measures. ... Read More



