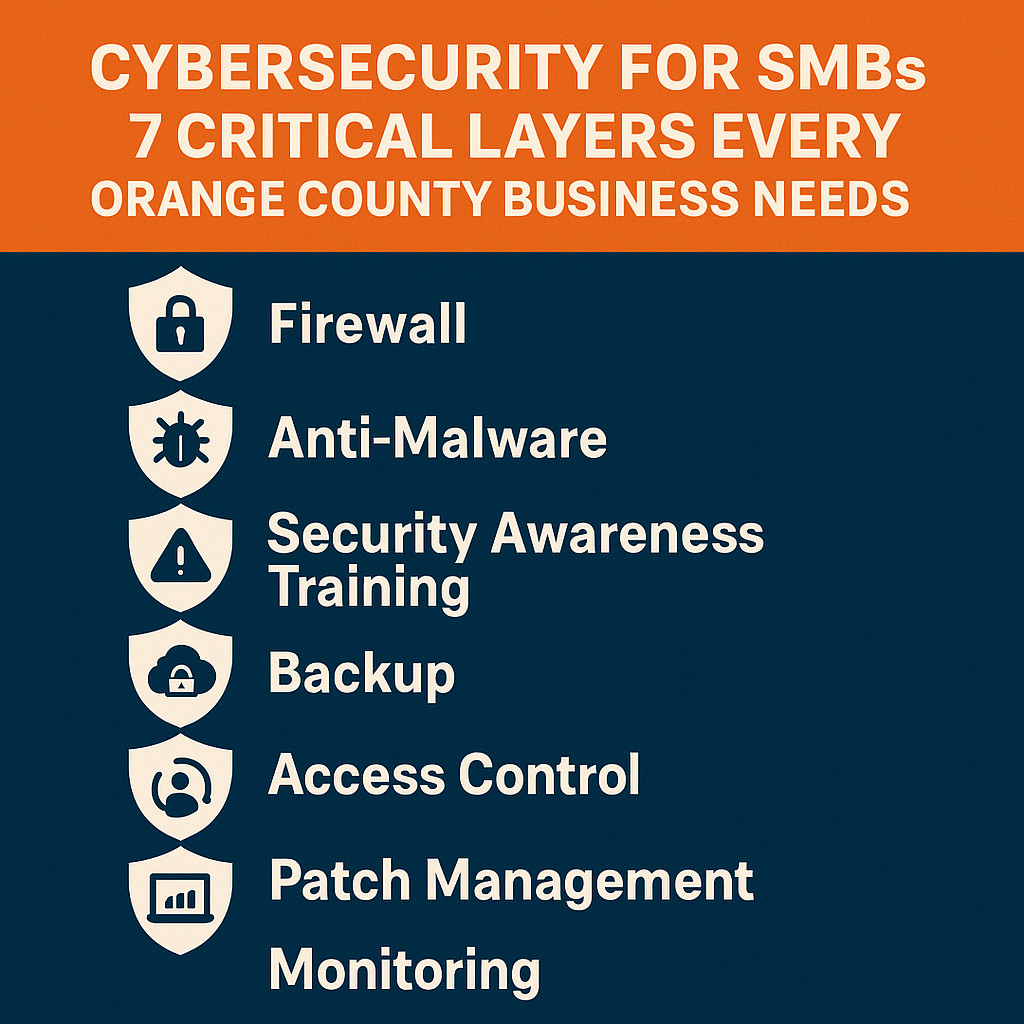
Business Continuity Planning in Orange County: How to Keep Your Doors Open—No Matter What
Business Continuity Planning (BCP) and Disaster Recovery (DR), specifically targeting businesses in Orange County, California. It emphasizes the critical need for proactive planning, noting that a significant percentage of businesses fail after major disasters due to inadequate preparation, which is particularly relevant given Southern California’s unique threats like earthquakes and wildfires. The text breaks down the core components of an effective BCDR strategy, including risk assessment, data backup (using RTO and RPO metrics), system redundancy, and continuous testing. Finally, the document promotes Technijian’s services, positioning the company as an expert partner offering comprehensive, managed BCDR solutions to help local small and medium-sized businesses achieve resilience and comply with various regulatory requirements. ... Read More