
Social Engineering Attacks: Protecting Human Weakness
Social engineering attacks exploit human psychology rather than technical vulnerabilities, making them one of the most dangerous forms of cybercrime. Attackers use tactics like phishing, pretexting, baiting, and tailgating to trick individuals into revealing sensitive data or granting unauthorized access. These schemes often rely on urgency, trust, or fear to manipulate victims. Businesses and individuals must recognize warning signs, provide security awareness training, and implement strong verification processes to stay protected. By combining education, multi-factor authentication, and monitoring tools, organizations can reduce risks. Defending against social engineering requires vigilance, awareness, and a culture of cybersecurity at every level.

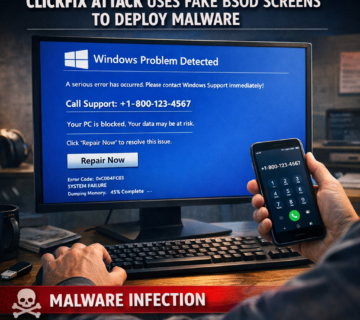
ClickFix Attack Uses Fake BSOD Screens to Deploy Malware

Workday Data Breach: What You Need to Know About the Recent HR Giant Security Incident
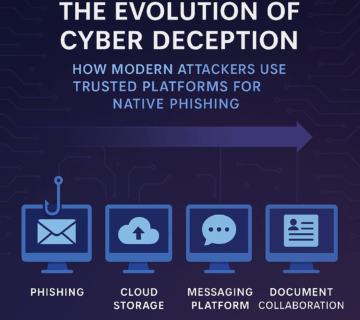
The Evolution of Cyber Deception: How Modern Attackers Use Trusted Platforms for Native Phishing
