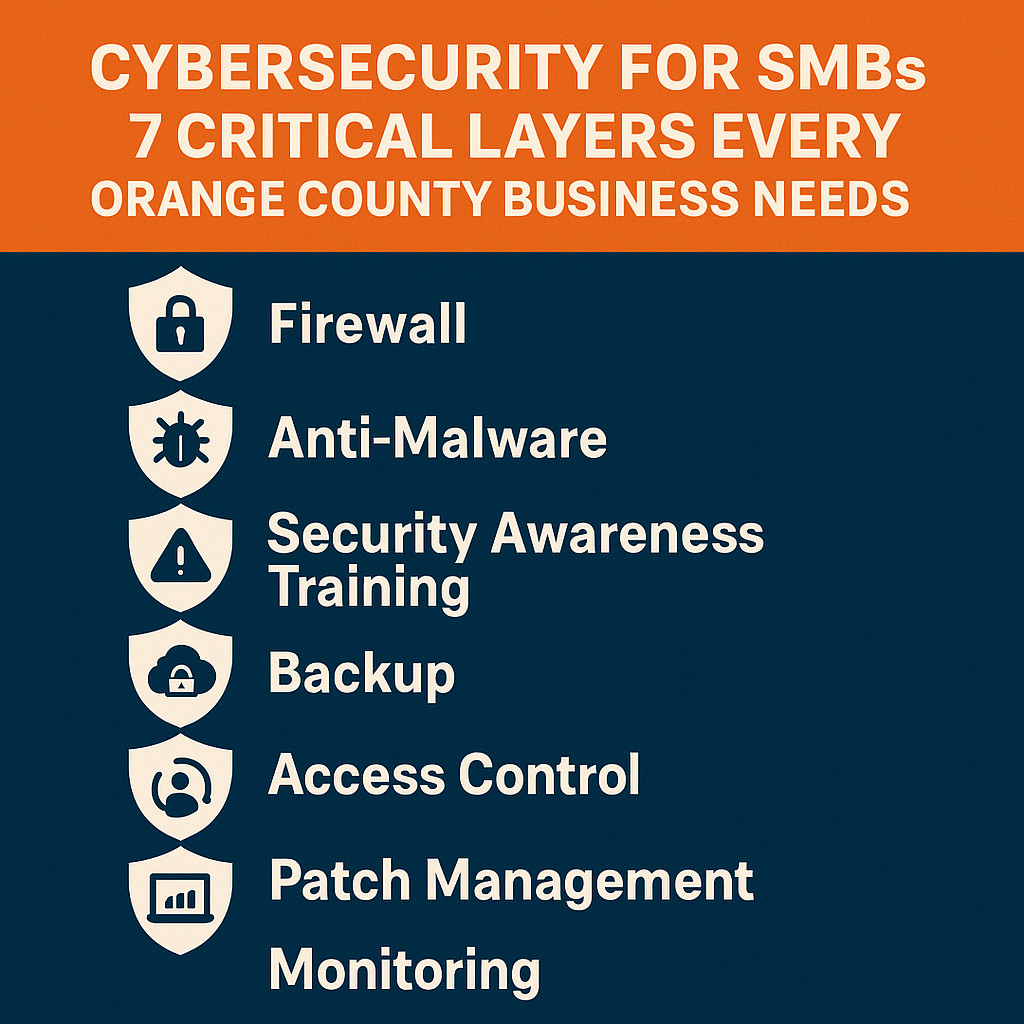
Cybersecurity for SMBs: 7 Critical Layers Every Orange County Business Needs
a defense-in-depth cybersecurity strategy specifically tailored for small and medium-sized businesses (SMBs), particularly those in Orange County, California. It emphasizes that SMBs are major targets for cyberattacks and must adopt a layered security approach to protect their assets. The guide meticulously outlines seven critical layers of cybersecurity, starting with email security and endpoint protection, and moving through network controls, access management, data backup, employee training, and continuous monitoring. Finally, the text positions Technijian, a local provider, as an expert partner for implementing this comprehensive security stack and assisting with industry-specific compliance requirements like HIPAA and PCI-DSS. ... Read More