New ErrTraffic Service Enables ClickFix Attacks Through Fabricated Browser Errors
🎙️ Dive Deeper with Our Podcast!
The cybersecurity landscape faces a troubling development as cybercriminals deploy a sophisticated new tool designed to exploit user trust through manufactured technical problems. ErrTraffic, a recently discovered cybercrime platform, represents a disturbing evolution in social engineering tactics by automating deceptive attacks that trick victims into compromising their own systems.
Understanding the ErrTraffic Threat
ErrTraffic emerged in late December 2024 on underground Russian-language hacking forums, marketed by a user known as LenAI. This malicious service operates as a self-hosted traffic distribution system that generates convincing fake website malfunctions to manipulate unsuspecting users. The platform carries a one-time price tag of $800, making it accessible to a wide range of threat actors.
What makes this tool particularly dangerous is its ability to seamlessly integrate into compromised websites. Once attackers gain control of a legitimate site or successfully inject malicious code, adding ErrTraffic requires only a single line of HTML. The platform then operates silently in the background, waiting for the right targets to arrive.
The system employs sophisticated filtering mechanisms that analyze visitor characteristics including geographic location and operating system details. Regular visitors who don’t match the predefined targeting criteria experience the website normally, seeing no indication of compromise. However, when a victim meeting the specific criteria lands on the infected page, the site’s Document Object Model undergoes modification to display artificial glitches.
How ClickFix Attacks Manipulate Users
ClickFix represents a category of social engineering attacks that manipulate targets into executing harmful commands on their own machines. The deception hinges on creating believable scenarios where users think they’re solving legitimate technical issues or verifying their identity.
These attacks have gained significant momentum throughout 2024, attracting both financially motivated cybercriminals and state-sponsored threat groups. The technique’s popularity stems from its effectiveness at circumventing traditional security measures, as victims willingly execute malicious code believing they’re fixing problems rather than creating them.
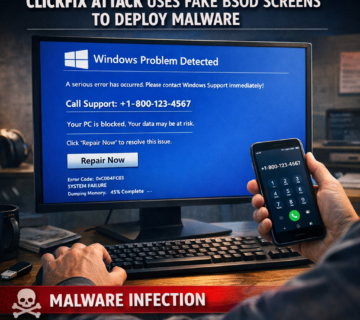
ErrTraffic takes this approach and industrializes it. The platform generates various types of fabricated problems including garbled text displays, font replacements with random symbols, false browser update notifications, and missing system font warnings. Each manufactured glitch appears authentic enough to convince users something genuinely needs fixing.
The Technical Mechanics Behind the Attacks
When victims encounter these artificial problems, ErrTraffic presents them with seemingly helpful solutions. These might include instructions to install browser updates, download system fonts, or execute commands in their system’s command prompt. The interface makes these actions appear necessary and harmless.
The actual danger lies in what happens when users follow these instructions. Behind the scenes, JavaScript code automatically copies a PowerShell command to the victim’s clipboard. When executed, this command initiates a download sequence that installs malicious software onto the compromised system.
The platform delivers different malware depending on the victim’s operating system. Windows users receive either Lumma or Vidar information-stealing malware. Android devices get infected with the Cerberus trojan. Mac users face deployment of AMOS, also known as Atomic Stealer. Linux systems receive unspecified backdoor programs.
Configuration and Targeting Capabilities
ErrTraffic provides attackers with a user-friendly control panel offering extensive configuration options and real-time campaign monitoring. Threat actors can specify exactly which malware gets deployed to each operating system type and define geographic targeting parameters to focus their attacks on specific countries or regions.
Interestingly, the platform contains hardcoded exclusions preventing attacks against systems in Commonwealth of Independent States countries. This built-in restriction likely indicates the geographic origins of ErrTraffic’s developers, following a common pattern among cybercrime tools created in Eastern European regions.
The platform reportedly achieves conversion rates reaching 60%, meaning that more than half of targeted users who encounter the fake glitches follow through with the malicious instructions. These remarkably high success rates explain why ClickFix tactics have become increasingly prevalent in the threat landscape.
The Broader Impact on Cybersecurity
Research teams monitoring credential theft ecosystems have identified concerning patterns in how stolen data gets utilized. In most documented cases, harvested information ends up for sale on darknet marketplaces where other criminals purchase it for various malicious purposes.
Additionally, attackers frequently leverage stolen credentials to compromise additional websites, creating a self-perpetuating cycle. Each newly compromised site becomes another potential host for ErrTraffic scripts, expanding the attack infrastructure and reaching more potential victims.
This cyclical pattern makes ErrTraffic particularly insidious. Unlike one-off attacks that require constant effort to identify new targets, this system creates its own opportunity pipeline. Every successful infection potentially leads to additional compromised websites, which then become platforms for further attacks.
The automation aspect fundamentally changes the economics of these attacks. Previously, executing convincing social engineering required manual effort for each target. ErrTraffic eliminates that limitation, allowing attackers to operate multiple campaigns simultaneously across numerous compromised websites with minimal ongoing effort.
Protecting Against ClickFix and ErrTraffic Attacks
Defending against these sophisticated social engineering tactics requires a multi-layered approach combining technical controls and user awareness. Organizations and individuals need to understand that legitimate technical problems rarely require copying commands into system terminals or downloading unexpected updates.
Browser updates always occur through official channels built into the browser itself, never through prompts on random websites. System fonts come pre-installed with operating systems, and any legitimate need for additional fonts would be communicated through official software sources, not compromised websites.
Users should maintain skepticism when encountering unexpected technical problems, especially if the suggested solution involves executing commands or downloading files. Taking a moment to close the suspicious website and access the same content through a direct URL or bookmark can help determine whether problems are genuine.
Organizations should implement robust website security monitoring to detect unauthorized code injections. Regular security audits, file integrity monitoring, and web application firewalls provide important defensive layers against the initial compromises that enable ErrTraffic deployment.
Security awareness training should specifically address ClickFix tactics and similar social engineering approaches. Employees need to recognize red flags including unexpected system messages, requests to execute commands, and pressure to act quickly on technical problems without verification.
The Evolution of Social Engineering Tactics
The emergence of ErrTraffic represents a significant evolution in how cybercriminals approach social engineering. Rather than crude phishing emails with obvious grammatical errors, modern attacks leverage sophisticated psychological manipulation backed by technical automation.
These tools lower the barrier to entry for conducting effective attacks. Previously, successful social engineering required skill in crafting convincing narratives and understanding target psychology. Platforms like ErrTraffic package that expertise into turnkey solutions that less sophisticated attackers can deploy effectively.
The trend toward automation and platformization in cybercrime mirrors legitimate software-as-a-service business models. Criminal entrepreneurs identify effective attack techniques, build tools that automate them, and then market these capabilities to a broader criminal customer base.
This industrialization of cybercrime creates challenges for defenders. The traditional approach of tracking specific threat actors becomes less effective when malicious tools spread widely among diverse criminal groups. Defense strategies must shift toward recognizing attack patterns and techniques rather than focusing solely on specific adversaries.
Frequently Asked Questions
What exactly is ErrTraffic and how does it work?
ErrTraffic is a cybercrime platform that generates fake technical problems on compromised websites to trick visitors into downloading malware. It works by modifying website displays to show artificial glitches, then offering malicious solutions disguised as fixes. The system automatically copies harmful commands to user clipboards, which install information-stealing malware when executed.
How can I tell if a website has been compromised with ErrTraffic?
Compromised websites typically appear normal until you match specific targeting criteria based on location and operating system. Warning signs include unexpected visual glitches, garbled text, suspicious browser update prompts, or messages claiming missing system fonts. If a website suddenly develops problems and suggests copying commands or downloading files to fix them, this represents a major red flag.
Which operating systems are targeted by ErrTraffic attacks?
ErrTraffic targets all major operating systems including Windows, macOS, Android, and Linux. Each platform receives different malware payloads specifically designed for that system. Windows systems get Lumma or Vidar information stealers, Macs receive AMOS stealer, Android devices get Cerberus trojan, and Linux systems receive various backdoors.
Why do these attacks have such high success rates?
ClickFix attacks achieve high conversion rates because they exploit natural user responses to technical problems. When people encounter what appears to be a legitimate website malfunction, they instinctively want to fix it. The attacks leverage this helpful instinct and present solutions that seem reasonable, making victims willing participants in their own compromise.
Can antivirus software protect against ErrTraffic attacks?
Traditional antivirus provides limited protection against these attacks because victims voluntarily execute the malicious commands. While some security software may detect and block the final payloads, the social engineering aspect bypasses many technical controls. The most effective defense combines security software with user awareness and skepticism toward unexpected technical problems.
What should I do if I suspect I’ve fallen victim to a ClickFix attack?
If you suspect compromise, immediately disconnect from the internet to prevent data exfiltration. Use reliable security software to do thorough malware scans. Change all passwords from a known-clean device, enable multi-factor authentication on all accounts, and monitor financial accounts for suspicious activity. Consider seeking professional cybersecurity assistance for thorough system cleaning and recovery.
How are organizations being targeted with ErrTraffic?
Organizations face risk through compromised websites they control or when employees visit infected third-party sites. Attackers often steal credentials from individual infections, then use those credentials to compromise corporate websites. This creates a cycle where each successful attack potentially enables multiple future attacks through newly compromised infrastructure.
What makes ErrTraffic different from traditional malware distribution?
ErrTraffic distinguishes itself through automation and integration. Rather than requiring constant manual effort to trick each victim, the platform automatically generates convincing lures tailored to each target’s system. It integrates seamlessly into compromised websites and operates continuously without ongoing attacker involvement, making it far more scalable than traditional approaches.
How Technijian Can Help
Protecting your organization against sophisticated threats like ErrTraffic requires comprehensive security strategies combining technical expertise with proactive monitoring and response capabilities. Technijian specializes in helping businesses defend against evolving cybersecurity threats through tailored solutions designed for your specific needs.
Our security assessment services identify vulnerabilities in your web infrastructure before attackers can exploit them. We conduct thorough audits of your websites and web applications, implementing robust monitoring systems that detect unauthorized code injections and suspicious modifications in real-time.
Technijian’s managed security services provide continuous protection with 24/7 monitoring by experienced security professionals. Our team stays current with emerging threats like ErrTraffic, ensuring your defenses evolve alongside the threat landscape. We implement multi-layered security controls including web application firewalls, intrusion detection systems, and advanced endpoint protection.
Employee awareness represents a critical defense layer against social engineering attacks. Our customized security awareness training programs educate your team about ClickFix tactics and similar threats, helping them recognize red flags and respond appropriately. We provide regular simulated attack exercises that test and reinforce security awareness without putting your systems at actual risk.
When incidents occur, rapid response makes the difference between minor disruption and major breach. Technijian offers incident response services with experienced professionals ready to contain threats, remediate compromises, and restore normal operations quickly. Our forensic capabilities help identify how breaches occurred and what data may have been affected.
Beyond reactive measures, we help organizations build resilient security architectures that withstand evolving threats. Our consultants work with your team to develop comprehensive security strategies aligned with business objectives, implementing defense-in-depth approaches that protect against both current and future attack techniques.
Contact Technijian today to schedule a comprehensive security assessment and learn how our expertise can protect your organization against ErrTraffic, ClickFix attacks, and the constantly evolving cybersecurity threat landscape. Don’t wait until after a compromise to take security seriously—proactive protection costs far less than incident recovery.
About Technijian
Technijian is a premier Managed IT Services provider in Irvine, specializing in delivering secure, scalable, and innovative AI and technology solutions across Orange County and Southern California. Founded in 2000 by Ravi Jain, what started as a one-man IT shop has evolved into a trusted technology partner with teams of engineers, AI specialists, and cybersecurity professionals both in the U.S. and internationally.
Headquartered in Irvine, we provide comprehensive cybersecurity solutions, IT support, AI implementation services, and cloud services throughout Orange County—from Aliso Viejo, Anaheim, Costa Mesa, and Fountain Valley to Newport Beach, Santa Ana, Tustin, and beyond. Our extensive experience with enterprise telecommunications and security deployments, combined with our deep understanding of local business needs, makes us the ideal partner for organizations seeking to implement solutions that provide real protection and operational efficiency.
We work closely with clients across diverse industries, including healthcare, finance, law, retail, and professional services, to design technology strategies that reduce risk, enhance productivity, and maintain the highest protection standards. Our Irvine-based office remains our primary hub, delivering the personalized service and responsive support that businesses across Orange County have relied on for over two decades.
With expertise spanning cybersecurity, managed IT services, telecommunications, AI implementation, consulting, and cloud solutions, Technijian has become the go-to partner for small to medium businesses seeking reliable technology infrastructure and comprehensive capabilities. Whether you need 3CX deployment in Irvine, telecommunications optimization in Santa Ana, or IT consulting in Anaheim, we deliver technology solutions that align with your business goals and operational requirements.
Partner with Technijian and experience the difference of a local IT company that combines global technology expertise with community-driven service. Our mission is to help businesses across Irvine, Orange County, and Southern California harness the power of advanced technology to stay protected, efficient, and competitive in today’s digital world.