Why You Need an IT Support Team in Anaheim with Authentication Expertise
How much does your IT support team in Anaheim know about internet security? If they lack a deep understanding of why authentication is a priority, it’s time to find a more advanced crew. Not only should your technical consultant be knowledgeable about the evolution of online security and cybercrime, they should be on the cutting edge of finding new solutions.
Keeping Up with Changing Technology
One of the key signs of a high-quality IT support group in Anaheim is they have a passion for staying on top of new solutions to block cybercriminals. If your team stopped learning about security a decade ago, your infrastructure is very vulnerable. Hackers keep discovering new ways to penetrate business networks, which is why you need to stay ahead of them.
The internet can be a place to enjoy all kinds of pop culture nostalgia, but that doesn’t mean vintage hardware or software is as timeless as a classic song or movie. In general, the older your system gets, the more vulnerable it will be to hackers, who prey upon outdated technology in which upgrades are no longer available.
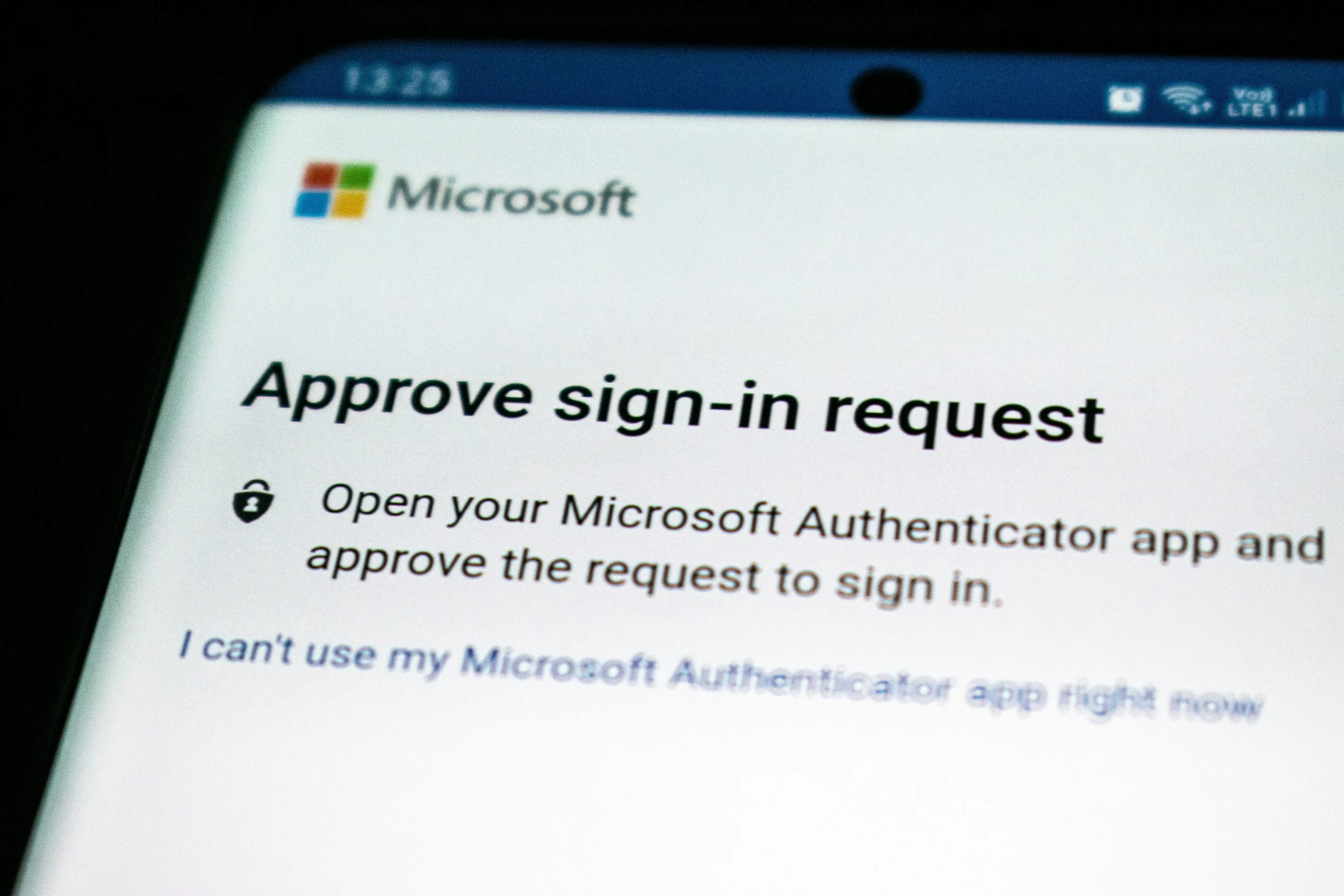
Modern Authentication Solutions
You can use the most expensive antivirus software on the market and still get hacked. In fact, if a financial giant like Equifax can get breached, so can any business that doesn’t take proper safety precautions. Authentication is a security strategy that includes passwords, PIN numbers, photo IDs, and encryption codes that verify a user’s identity. Here are some of the characteristics for reliable and safe authentication:
- Easy to use
- No simple short passwords
- Alphanumeric passwords with variety in upper/lower case and special characters
- No distribution of authentication data to others
In recent years, IT experts have moved toward implementing double authentication, meaning more than one factor for gaining access to a digital resource. A newer development is the emergence of biometric authentication, which means using physical traits of an individual, such as fingerprints, facial or voice recognition software, and DNA. Apple’s iPhone X has helped usher in facial recognition solutions.
Will hackers learn to breach even biometric safeguards? If the past is any indication of the future, then the answer is “probably, but not right away.” Ideally, by the time hackers figure out the latest technology, a newer solution will take its place. China, for example, is currently replacing passwords with recognition software apps from Face++ that are 99.50% reliable.
You need to choose your IT support team in Anaheim carefully to outsmart and block hackers. Contact us now at Technijian to learn more about how we can strengthen your security and other business technology.